At the beginning of October 2022, Microsoft made changes to the University email service. As a result, some email clients were no longer able to access emails on the University's servers. This page explains the change.
Background
The University email service is based on Microsoft Exchange. Exchange servers can communicate with email clients in a number of ways. Modern clients, especially those produced or supported by Microsoft and Apple, can use Exchange-specific protocols to access the server, and will be unaffected by these changes. Clients which do not support the MS protocols use older open standard protocols such as POP and IMAP and SMTP for access. These are affected.
In the past, these clients have been able to use what Microsoft calls "basic auth" to access the server. This means that the client simply provides the server with a username and password for authentication. As a security measure, Microsoft has turned this mechanism off. Since then, mail clients have needed to use the "OAuth2" authentication mechanism instead - at least when they access the University mail servers via POP or IMAP, or send mail via SMTP.
All modern Microsoft mail clients such as the Office 365 web mail client (the University's recommended client), Outlook 2016 or newer for Windows or Mac, and the Windows 10 and 11 mail apps are unaffected.
The default mail apps on up-to-date versions of macOS, iOS/iPadOS and Android will also continue working, especially when configured to use the Exchange protocol - though Microsoft advise that on mobile clients you may need to delete and recreate your mail account after the change is made.
Thunderbird is explicitly not supported by the University, but it supports OAuth2 for IMAP and will work after some reconfiguration.
Command line clients Alpine and Mutt can be made to work with OAuth2 - see below for some details.
What if an Email Client isn't Mentioned Above?
If your favourite email client isn't mentioned above, then you will need to carry out some investigations to see if it can be used with the University mail service. Check whether it offers native Exchange support (very few clients that don't come from Microsoft will do this). If it doesn't offer native support, then it is almost certainly using the IMAP protocol to access the Exchange server, so you will need to check whether the client supports IMAP authentication via OAuth2. If it doesn't, then it's time to start planning a move to an email client which will continue working. Computing support may be able to offer advice on migrating to a supported mail client.
Please note that Informatics computing support can offer little or no assistance in getting unsupported mail clients working. Please also note that turning off basic auth is not a School or even University decision but is being applied to Exchange servers across the globe by Microsoft.
Some client-specific advice
Alpine
Versions of Alpine newer than 2.24 (DICE Ubuntu currently provides 2.26) can be configured to used OAuth2 with IMAP. Some details:
- Create a password file with:
touch ~/.pine-passfile
- Reconfigure alpine by ensuring your connection string ends like:
user=<UUN>@ed.ac.uk/auth=xoauth2
That is, add the /auth... bit.
Depending on your alpine setup,
user=<UUN>
may appear several times. The main entry to get mail working is "Inbox path" and should look something like:{outlook.office365.com/ssl/user=<UUN>@ed.ac.uk/auth=xoauth2}<PATH TO INBOX>But if you have additional mail folders on Office 365 you will need to alter these too via
[S]etup, Collection[L]ists. Alter each collection which referencesoutlook.office365.comto include/auth=xoauth2.If you are using the University SMTP server for outgoing mail, you will also need to set SMTP server to something like:
outlook.office365.com/submit/user=<UUN@ed.ac.uk>/auth=xoauth2
If you are using the University SMTP server, make sure that you are not using the Customized Header Config setting to set a different From: address. If you are, attempts to send mail will fail with an "error 250" message.
- Save all these changes and try to access your University mail account. You will need to enter your University mail password at this point if you have not already done so. Alpine should display a code and a Microsoft URL to visit. Visit the web site, enter the code and when prompted log into your Office365 account and grant Alpine access.
- Return to your Alpine window and press Y to store the token. There might be a delay of even 30 seconds before Alpine reacts after the code was entered on the Microsoft website. Alpine will prompt you to create a master password for your new passfile. DO NOT use your DICE or University password.
- To avoid inadvertently saving other passwords in the passfile, we recommend now setting the configuration variable
[X] Disable Password File Saving.
in alpine. This doesn't prevent O365 tokens from being renewed, but it avoids prompts to save passwords for other servers.
Subsequent logins will simply ask for your passfile password, which may be easier to remember than your DICE or University password as it's "only" unlocking a token which itself can only access your email under limited circumstances. DO NOT use your DICE or University password as your passfile password.
Mutt
Mutt 2.0 has OAUTH support: http://www.mutt.org/relnotes/2.0/
The following external pages provide useful information on how to configure mutt to support OAuth 2.0 authentication for Office 365:
- https://howto.cs.uchicago.edu/nix:mutt
- https://www.vanormondt.net/~peter/blog/2021-03-16-mutt-office365-mfa.html
- https://www.redhat.com/sysadmin/mutt-email-oauth2
You will need to run a script to manage the token file. Save the file into your home directory, rename it appropriately and make it executable:
wget https://computing.help.inf.ed.ac.uk/sites/default/files/mutt_oauth2.py_.txt -O mutt_oauth2 chmod u+x mutt_oauth2
This script requires you to have a gpg key that is used to encrypt/decrypt the token file. If you do not already have a gpg key you can generate one like this:
gpg --gen-key
Use a secure passphrase. Once you have a gpg key, edit your mutt_oauth2 script to replace the YOUR_GPG_IDENTITY string with that ID (it's in the ENCRYPTION_PIPE setting, fairly near the top of the file).
To get a token for the first time you need to run the script like this:
mutt_oauth2 ~/.mutt/oath2_token_file --verbose --authorize
You need to specify the location for the token file and it must not already exist, if the script fails the first time you run it, then you may need to manually delete that file before having another attempt.
You will be prompted to provide a few details, here's what seems to work:
Available app and endpoint registrations: google microsoft
OAuth2 registration: microsoft
Preferred OAuth2 flow ("authcode" or "localhostauthcode" or "devicecode"): localhostauthcode
Account e-mail address: UUN@ed.ac.uk
Where you, obviously, need to replace UUN@ed.ac.uk with the username you normally use to login to O365. This will produce a URL that you need to visit in your web browser. Once you have successfully authenticated via your browser you should see some output like this:
NOTICE: Obtained new access token, expires 2022-12-05T11:30:17.824332.
and a long access token string, the script will have stored the token in the specified token file. You are now ready to go! The final step is to configure mutt, you need something like this:
set folder = 'imaps://outlook.office365.com/' set imap_user = 'UUN@ed.ac.uk' set imap_authenticators = 'xoauth2' set imap_oauth_refresh_command = "~/mutt_oauth2 ~/.mutt/oath2_token_file"
Again, replace UUN@ed.ac.uk with your account details and specify the correct paths to your script and token file.
Thunderbird
Setting up OAuth2 in Thunderbird is easy to do. While in the Server Settings dialog box, either while changing the settings of an existing account or setting up a new one, change the Authentication method dropdown to OAuth2 as seen in the image.
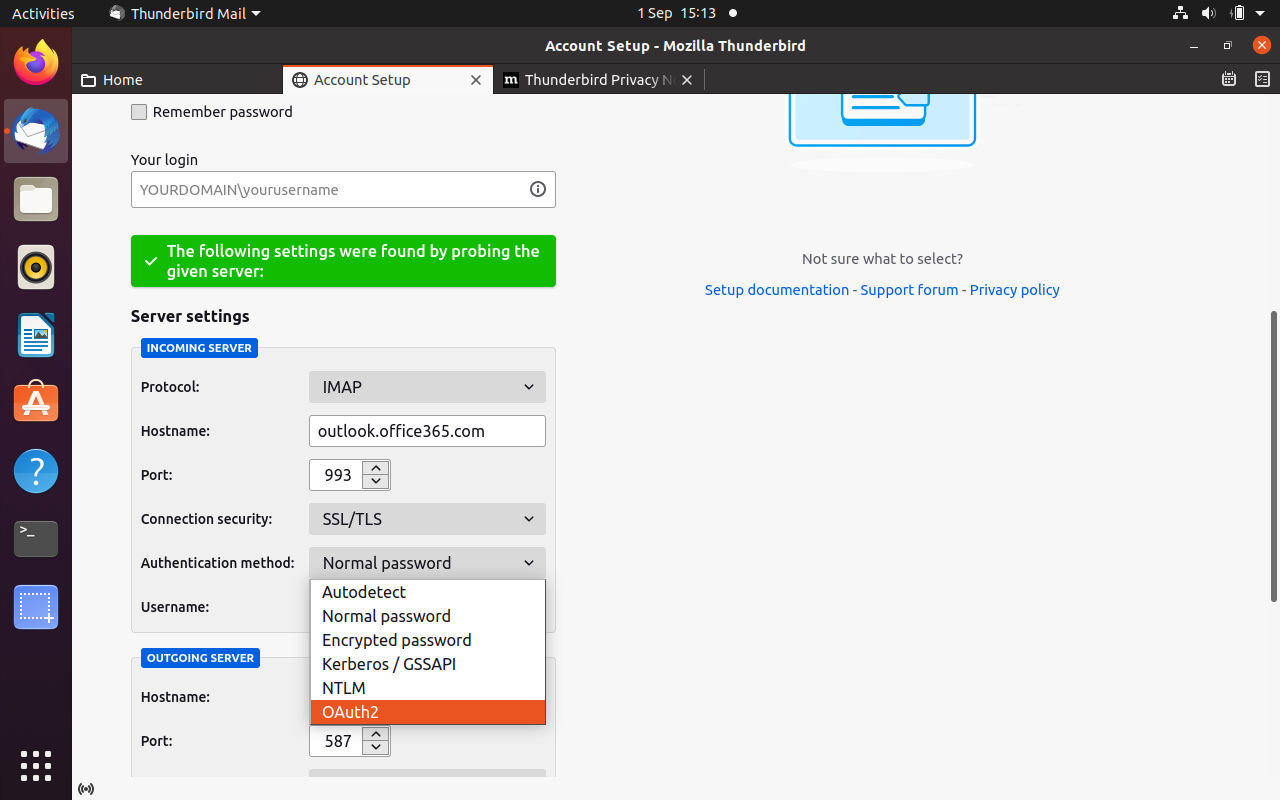
Note that when setting up an account, the OAuth2 option won't appear until you have set up the hostname, port and connection security of the server using the settings found in the IS documentation. Remember to specify OAuth2 as the authentication method for both the IMAP and SMTP servers.
Other clients
If we receive any useful information on getting other clients working, we will add it here. It you have any information which you think would be useful for other Informatics users to know, get in touch!
